With an on premises Active Directory despite Privileged Access Management tools being available, the sad fact was that accounts would be put in to Domain Admins or other groups with high privileges and live there permanently. Sometimes for years and years after the associated person left.
Surely things would be better in the cloud? A little maybe but we see when performing Security Audits, clients who have too many users permanently sitting in Global Administrators or accounts that are permanently assigned other highly privileged roles. Microsoft Privileged Identity Management (PIM) can help with this by greatly simplifying the management and monitoring of cloud identities and this blog gives a brief overview of PIM benefits:
Microsoft PIM can apply to two areas –
Azure AD (Think Global Admins, Security Admins, Intune Admins on Azure AD accounts)
Azure resources (Think Owner, Network Contributor, Virtual Machine Contributor on subscriptions for example)
PIM applies to administrative roles only and there are some license requirements: admin accounts that use PIM will require Azure Premium P2 / Microsoft Enterprise Mobility + Security (EMS) E5 or Microsoft 365 E5 license. (There are some PIM tasks that don’t require this (policy configuration and setting up of access reviews) but the majority of use cases do).
Microsoft recommend that both for on-premises and cloud-based solutions, administrators are given the minimum rights and and access permissions to be able to do their jobs. Once PIM is set up, accounts should operate as a standard user, requesting higher privileges in the PIM console either in Azure AD or on resources when specifically needed. Also an approval process where a person or group of persons can assess the request and say yes or no can be wrapped around. PIM is critical in reducing the potential attack surface for organisation – if your account can only do damaging things for a defined time period, and require verification you are who you claim to be whilst recording when you tried to do it this also gives us a lot more visibility and control. And actually when I go in to places I am perfectly happy to use PIM and only be granted the roles I need, I am over the moon if it is not possible to do things I don’t need to do!
Accounts can be configured in PIM to be eligible for a role period of time, e.g. for the duration of a work project say 2 months or permanently. Activating a role can be configured specifically to require MFA (admins should be using this anyway hopefully), to need an input of justifications and if required, approval for the role through an approval group.

The periods users hold an active role can also be defined, e.g. for a working day / half working day depending on the types of tasks a person with that role would do and how long they would take, so there is an important factor prior to configuring this of understanding how those using privileged roles do their jobs; will their portal access bomb out in the middle of a critical operation. Access reviews can be configured and scheduled in PIM, this allows us keep tabs on who has a role, if they have signed in recently and if required, provide recommendations for culling! Access Reviews can even automatically take action such as remove users from the role.
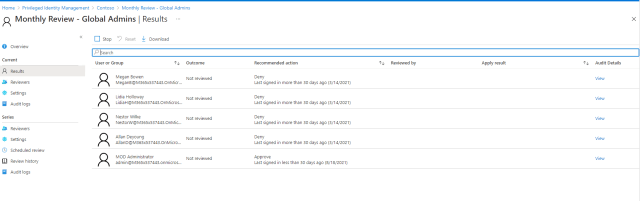
30 days worth of PIM audit data, e.g. who activated a role, when, when was it deactivated can be viewed in Azure. To keep data for longer, the information can be passed to an Azure Storage account.
It is also key when rolling out PIM to keep impacted admin teams in the loop. If they go from having permanent access – e.g. just being able to go straight to the area of Azure where they do their work to then having to follow a different process, this can be a shock if not communicated well in advance.
