This is part 3 of a series of articles on the key themes from Microsoft Ignite, March 2021:
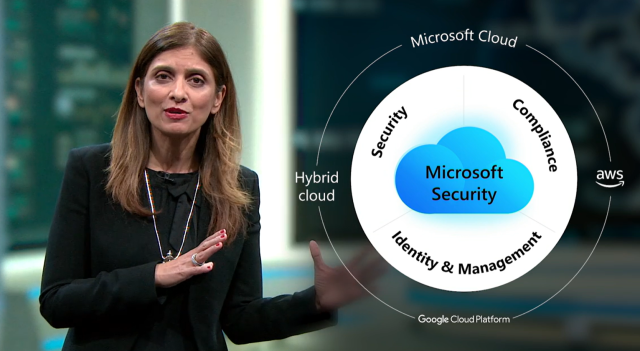
This blog post focusses on the Microsoft announcements for Security and Compliance at Ignite. Microsoft’s Corporate Vice President of Microsoft Security, Compliance and Identity, Vasu Jakkal, kicked of this keynote by introducing what Microsoft means when it says “Security for all”.
Microsoft want to make our digital world safe for everyone by providing security that reflects, empowers, and includes everyone. When Microsoft says security for all it really means all:
- All organisations, big and small
- All your data
- All clouds (Azure, AWS, GCP etc)
- All your people (wherever they are)
- All your devices and platforms
- All the risks you face
- All the opportunities ahead
As always, there is an evolving threat landscape. Microsoft gather over 8 trillion security signals a day and have seen an increase in cybercrime, ransomware, and nation state attacks. These have been led by attacks emanating from Russia, but also Iran, North Korea, and China. Microsoft produced a Digital Defence Report in September 2020 that describes the current threat intelligence landscape. It also provides guidance and insights from experts, practitioners, and defenders at Microsoft.
Solorigate was an incredibly sophisticated nation state attack that targeted the SolarWinds Orion software. FireEye found it and asked Microsoft to help investigate. Using the 8 trillion signals they could find the traces/footprints and then could highlight it to customers. Microsoft don’t just sell security software or respond to threats, it is working to reduce digital crimes, disrupt botnets, and nation state actors. You can read more about Microsoft’s analysis of Solorigate/NOBELIUM on its security blog.
A combined approach
Microsoft take a combined approach to Security, Compliance, Identity and Management. This combined approach reduces risk when compared to managing these elements in silos. The services they provide are designed not to slow people down or stifle business innovation and are designed around their zero trust principles:
- Verify explicitly. Always authenticate and authorise based on the available data points, including user identity, location, device, service or workload, data classification, and anomalies.
- Least privileged access. Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive policies, and data protection to protect both data and productivity.
- Assume breach. Segment access by network, user, devices, and application. Use encryption to protect data, and use analytics to get visibility, detect threats, and improve your security.
Microsoft have a great 30-minute module on its free Microsoft Learn platform that goes into zero trust and other fundamental security concepts: Describe the concepts of security, compliance, and identity.
Identity is the first line of defence. Passwords are still the weakest link in any application and Microsoft are encouraging organisations to “go passwordless”. 200 million customers are already signing in with work or Microsoft accounts without passwords. Instead, they are using Windows Hello, Microsoft Authenticator and FIDO2 keys. Microsoft announced a couple of new features for Azure Active Directory.
- Conditional Access is getting even smarter by having authentication context (now in public preview). This allows even more granular policies at the application level. For example, a Conditional Access policy for Outlook may allow users to log in and send an email but won’t let them download a file.
- Passwordless Authentication has left the preview stage and is now generally available.
- The new Temporary Access Pass feature is in public preview. This removes the need for passwords even in a lockout/reset scenario.
- See even more identity announcements from Ignite on the Microsoft Security blog.
Use Sentinel and Defender to decrease fragmentation
Complexity of apps and infrastructure causes risks like Solorigate. Fragmentation between different security tools introduces risk that a key signal could be dropped or misinterpreted between them. Azure Sentinel and Microsoft Defender aims to unify all security services from a consistent well integrated management plane.
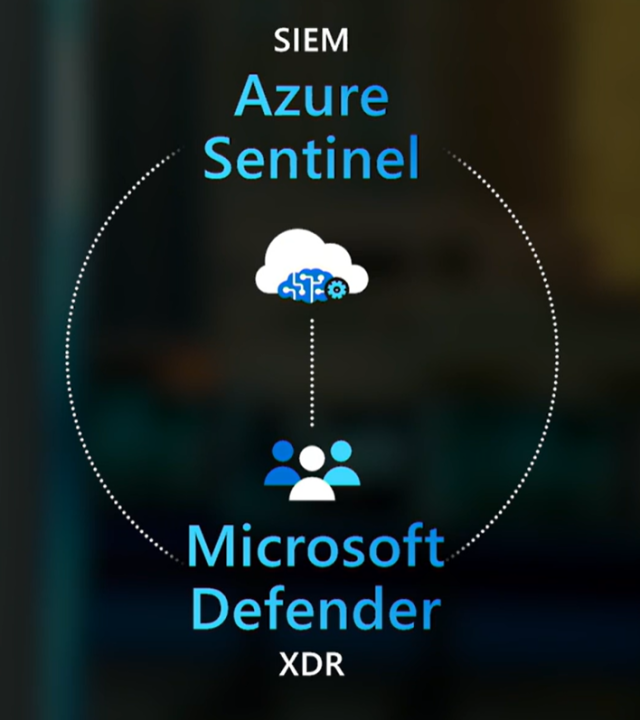
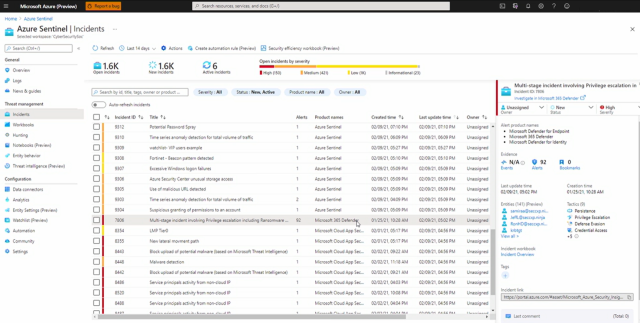
Sentinel is now a leader in the Forrester Wave for Security Incident and Event Management (SIEM) and is the world’s only cloud-native SIEM. Organisations that have tried and failed to introduce SIEM tools in the past have often cited costs and alert fatigue as issues. Forrester found Sentinel is 47% lower cost than legacy SIEMs and reduces 78% more false positives. At this Ignite, Microsoft announced 30 new connectors for Sentinel including Salesforce, Cisco Umbrella and VMWare. Integration between the services is also improving. Defender and Sentinel now share incident views, schema and integrated UX (note the highlighted product name in the screenshot). Clicking “investigate” jumps you into the Defender portal.
Microsoft also launched new Threat Analytics as part of M365 Defender. This service delivers curated threat intelligence reports from expert Microsoft security researchers. The service highlights risks like the Solorigate attack, describes what they are, insight to whether they are threats in your environment, and how to mitigate against them.
Inside-out risks
Of course, information risks don’t always come from the outside-in but also from the inside-out. Microsoft is extending its compliance capabilities out to 3rd parties. They also announced some new functionality:
- Microsoft Information Protection – you can now co-edit while a document stays encrypted, even across different operating systems like Word for Mac and Windows.
- Data Loss Prevention – DLP policies can now be set for the new Microsoft Edge browser, and they are extending this to also cover Google Chrome too
- Purview – Scan and classify data in AWS S3 buckets and other Azure connected data sources. This allows you to scan and label data in the M365 Compliance Center and then use Purview to get a holistic view of that data
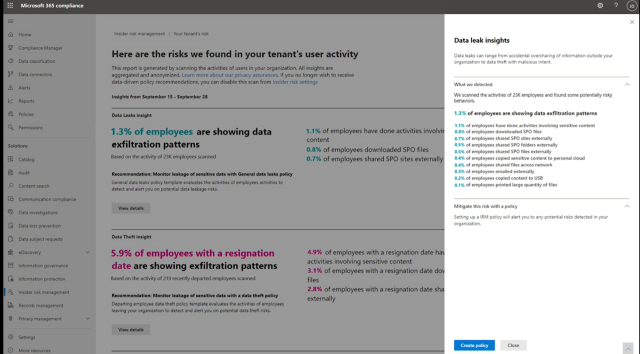
The final announcement was on new Insider Risk Management Analytics. With one click you can scan tenant audit logs to discover potential risky activity. It will also provide insights to help you customise your info risk policies to better meet your needs.
Conclusion
My key takeaway from this session is that improving an organisation’s security posture is a journey. As the risks keep evolving, so must your security practices. Microsoft takes security very seriously and I feel like I can trust them to do a fantastic job of keeping its services secure but it is a shared responsibility with each organisation to do their part in protecting their employees and information. Resiliency is often themed around backups, high availability, and disaster recovery but I see increasing your layers of security as another key pillar to that.
Microsoft ended this session with a call to action:
- Protect your identities – use MFA
- Manage your device health – keep them current
- Assess your security posture – review and understand your secure score
- Strengthen your compliance posture – with Compliance Manager
- Get your security certification – 4 new exams for security
I can’t agree more! Remember, progress is better than perfection and increasing security is all about adding those extra layers where you can.
I’ve been on my own personal journey for step 5 above. I recently went through the free Microsoft Learn course on Security, Compliance and Identity Fundamentals. This was key in helping me pass exam SC-900 and get certified. The course itself (like most of the “fundamentals” series) is a fantastic way to get to grips with all the different services and features on offer. I often fine the way these courses are structured easier to understand than just diving straight into the official documentation.

risual are here to help if you are looking to address security and compliance risks in your organisation. Contact us to find out more about our range of advisory and management services including:
- Zero Trust strategies
- Sentinel and Microsoft Defender quick starts
- CyberEssentials review and recommendations
- Security Operations Centre (SOC) managed service
This article first appeared on Thom’s Headspace | You can find Thom on twitter @thommck
